The SAKA has many web services for processing transaction using ANSI X-924.1 keys. But before those keys can be used, they must loaded into the appliance. SAKA supports two methods for loading Base Derivation Keys (BDKs)—one for temporary storage and one for persistent storage. Additionally, SAKA can store Local Terminal Master Keys (LTMKs), Terminal Master Keys (TMKs), and Terminal PIN Keys (TPKs) using persistent storage.
SAKA includes a client application—the Key Management Server Console Tool (KMSConsoleTool)—that allows KCs to load ANSI keys into temporary or permanent storage from remote locations. KCs just need a connection to SAKA from their computers and their Key Component and Key Check Value (KCV) from the ANSI Key.
While it is recommended that KC connections be controlled through an access control list of a router or switch to prevent denial-of-service attacks, the connection need not be secured for confidentiality since SAKA accepts KC commands and responses only over a secure transport protocol—Transport Layer Security.
The installation process of the SAKAs would have resulted in the KCs being given the KMSConsoleTool on some media that they would use to install on their computers. Since the KMSConsoleTool is a Java application, it can run on any platform where a Java Virtual Machine (JVM) is available. It is, however, necessary for the KCs to have a supported version of the JVM on their computer to use the tool. See Chapter 1 for the supported version of the JVM for your appliance.
On a Windows PC, the KCs would use a Command Tool script (a batch file) to start the KMSConsoleTool. On a Linux computer, this would be a shell script. The script file can be associated with an icon on the KC's desktop to make it convenient for the KC to use the tool.
When the KMSConsoleTool is started, it presents the following screen:
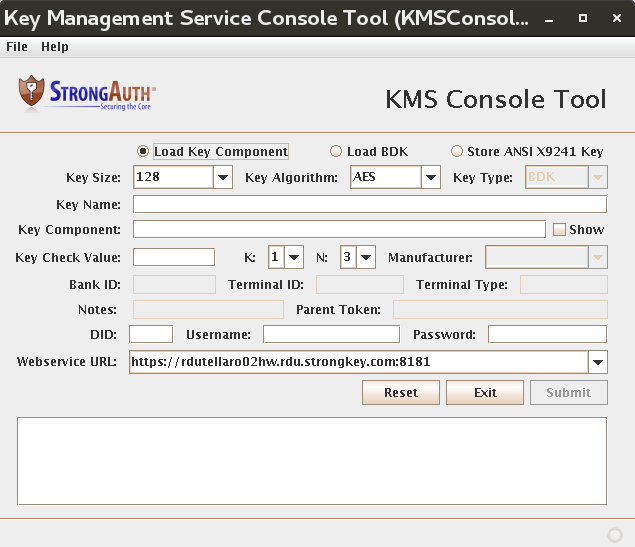
Complete the fields as described in the table below.
|
Load Key Component/Load BDK/Store ANSI X9241 Key |
The KMS Console performs three main key management tasks:
These radio buttons specify which task the KMSConsoleTool should perform. |
|
Key Size |
The size of the key to be stored in the SAKA. |
|
Key Algorithm |
The algorithm associated with the key being stored. When this stored key is referenced by other web service calls, this algorithm will be used exclusively with this key. |
|
Key Type |
The type of key that is being stored in the SAKA. |
|
Key Name |
A user-defined name to associate with this key or Key Component being loaded into the appliance. When loading multiple Key Components from a set, all Key Components must have the same key name. |
|
Encrypted Key |
The hex-encoded, wrapped ANSI key to be stored in the SAKA. |
|
Key Component |
The hex-encoded Key Component to be loaded into the appliance. |
|
Show |
Allows the user to view the Key Component being typed (normally hidden by default). This allows a Key Component custodian to check whether they have made any typos. Care must be taken to ensure only the Key Component custodian is able to view the plaintext Key Component. |
|
Key Check Value |
A hex-encoded string representation of a KCV. When loading a Key Component, this KCV belongs to that Key Component. When loading a BDK or storing an ANSI key, this KCV belongs to the assembled/decrypted key. |
|
K |
A numerical identifier for this Key Component in the set of Key Components. |
|
N |
The total amount of Key Components in this set. |
|
Manufacturer |
When loading a BDK, the manufacturer associated with this BDK. |
|
Bank ID |
A numeric identifier for with which bank this key is associated. |
|
Terminal ID |
An optional numerical identifier for with which terminal this key is associated. |
|
Terminal Type |
An optional string identifier for to which type of terminal this key belongs. |
|
Notes |
User-defined notes to be stored alongside the key. |
|
Parent Token |
The token identifier of the wrapping key used to encrypt this ANSI key. |
|
DID |
The unique encryption domain identifier. |
|
Username |
The username (service credential) within the encryption domain with the authorization to call this web service. |
|
Password |
The password of the username to authenticate the requeter's credential. |
|
Webservice URL |
Every SAKA listens to KMS commands at a specific URL. This is established at installation of the SAKA. The KC should specify this URL in this field. SAKA always uses the TLS protocol, so the URL must begin with https. |
|
Reset |
This button resets all values to the defaults on the tool's panel. |
|
Exit |
Exits the KMSConsoleTool. |
|
Submit |
Disabled by default. If all appropriate fields are filled in on the form, the button is enabled. Selecting it submits the activation command to KMS. Once completed, feedback is provided on whether the command succeeded. |
