Once you have a migration key from saka01, that EDK can be imported into saka02. After starting KMTool on saka02 appliance, all Key Custodians and the Domain Administrator must validate their credentials with KMTool.
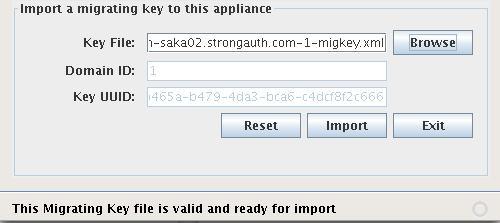
After all KCs and the DA are validated, the Import a migrating key to this appliance panel will be unlocked. This panel allows you to specify a migration keyfile from saka01 and import it into saka02:
|
Key File |
The filename of the migrating key generated on the saka01 appliance. |
|
Domain ID |
The encryption domain identifier for which the key has to be migrated; this is automatically filled out by the tool. |
|
Key UUID |
The UUID created while generating the key; this is automatically filled out by the tool and helps verify the unique ID of the migrating EDK. |
In the previous section, we created a migration key name saka01.strongauth.com-saka02.strongauth.com-1-migkey.xml. Yours will be named differently depending on the names of your appliances and to and from which domains you are migrating.
-
Browse to and select a keyfile.
-
After selecting the file, click Import to import this key into saka02. If the process works correctly, you will see a message indicating success: “Successfully imported migrating key to this SAKA.”
 NOTE: Additional EDKs can be imported from other domains before closing KMTool. To import another EDK, validate the DA from the extra domain (don't forget to change the DID field). After validating the domain, click Import again to import another migration key for this extra domain. This process can be repeated for each other domain.
NOTE: Additional EDKs can be imported from other domains before closing KMTool. To import another EDK, validate the DA from the extra domain (don't forget to change the DID field). After validating the domain, click Import again to import another migration key for this extra domain. This process can be repeated for each other domain. -
Click Exit to close KMTool.
This concludes the key migration process and you can exit KMTool. The saka02 appliance is now capable of decrypting objects encrypted by other appliances within the trusted cluster.
