Whether this is a full HSM recovery or an incremental database recovery, at this point you should have an HSM with the correct MBK loaded. Before restoring the encrypted backup, make sure you have file system access to the encrypted backups whether they are in a folder such as /root/backups or an external USB device.
-
Ensure a Login State of 22000000 in CAT by logging in up to two administrators if necessary.
-
Click the menu option Manage → Backup/Restore. Restore the HSM databases by clicking on the ‘Backup/Restore’ option. Select ‘Restore databases from Backup directory to Target CryptoServer’ option and select the directory that has the databases that were backed up from the primary server
(Backup USB's). Make sure to select both the CXI and Users databases from the list.
-
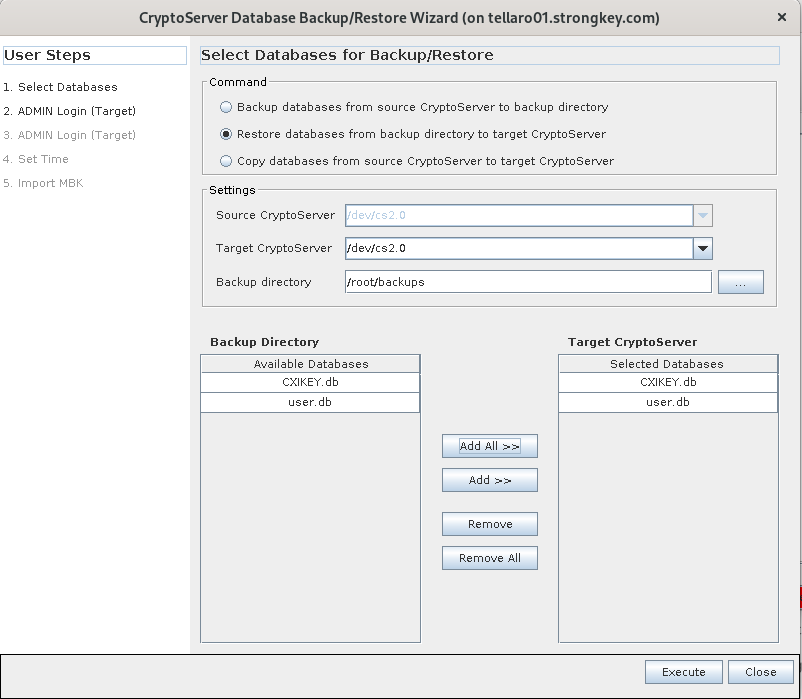
The CryptoServer Database Backup/Restore Wizard allows control over the type and specifications of the operation to be performed. The Command to create the backup is Restore databases from Backup directory to Target CryptoServer. The Target CryptoServer will be
/dev/cs2.0. Select the backup directory—either a local folder such as /root/backupsor the path to a mounted USB device. Click Add All >> to see bothCXIKEY.dbanduser.dbadded under Target CryptoServer. Once finished making these changes, click the Execute button. -
If the import is successful, you will be shown a list of imported files:
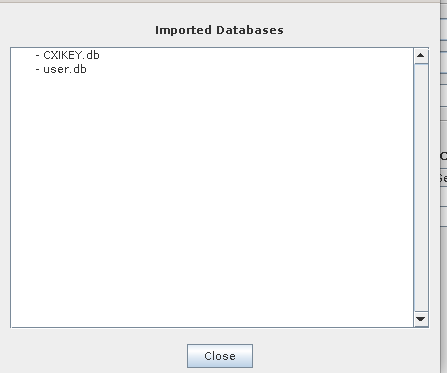
This process will import all new content from the encrypted database backups into this HSM.
NOTE: Any administrators you already have on this HSM will not be deleted to match those administrators in the user.db backup. This means if the default ADMIN is on the HSM, or if any other HSM admin is revoked and replaced, then the extra administrators will need to be deleted after this step. See the process for Deleting an Admin for more details.