- Versions
- Release Notes
- Preface
- KAM Introduction
- Architecture
- Installation
- Preliminary Steps
- Install Components (Primary)
- Install Components (Secondary)
- Define KCs (Primary)
- Verify KCs (Secondary)
- Set Personal Identification Numbers (PINs) [Primary]
- Set PINs and Complete Key Migration [Secondary]
- Create System Users [Primary]
- Create a New Encryption Domain [Primary]
- Complete Second Domain Key Migration [Secondary]
- Add System Users [Primary]
- Configure the SKCE domain [Primary]
- Replicate the CEM Domain [Secondary]
- Back
- CCS Web Service Operations
- KAM Web Service Operations
- KMS Web Service Operations
- CCReturnObject
- CCKeyComponentType
- CCCryptographicMaterialType
- CCEncryptedAnsiX9241KeyType
- KMS Module loadKeyComponent Mechanics
- KMS Module loadBaseDerivationKey Mechanics
- KMS Module generateBaseDerivationKey Mechanics
- KMS Module generateInitialKey Mechanics
- KMS Module storeAnsiX9241Key Mechanics
- KMS Module replaceAnsiX9241Key Mechanics
- KMS Module deleteAnsiX9241Key Mechanics
- KMS Module updateAnsiX9241Key Mechanics
- Back
- KAM Batch Operations
- KAM DemoClients
- KAM KCSetPINTool
- KAM DACTool
- KAM Key Migration Tool
- KAM KMS ConsoleTool
- KAM Configuration
- KAM Key Management
- HSM Integration
- Managing Credentials
- Changing Hostname and IP
- Internal Repositories
- Internal Repositories Rocky 9.x
- Appliance Security
- PCI DSS 3.2
- PCI DSS 4.0.1
- KC Responsibilities
- Add New SKCE Domain
- KAM Replication
- Appendices
- Adding a Disaster Recovery Backup (DRB) Node to a Cluster
- Adding an Additional Server to a Cluster
- Application Development Guide
- Batch Delete Tokens
- CIS Hardening Verification RHEL 7.X
- CIS Hardening Verification ROCKY 9.X
- Cleanup SAKA Disk Space
- Configure Syslog
- Create Software Keystore HSM Credential
- Installing KCSPTool and DACTool on Windows
- KA Replace EOL Node
- KAM KC Replace Tool
- MariaDB Audit Logging Configuration
- Migration Information
- Migrating from Centos to Rocky
- Modifying the Appliance's IP Address or Hostname
- Reboot StrongKey Tellaro
- Relay Webservice
- Replace CMOS Battery
- Setting up LACP Bonding on Tellaro KA
- Strongkey Tellaro & Ransomware Protection
- Using Custom SSL/TLS Certificates
- Using a Custom Trust Store
- Using HAProxy as a Load Balancer
- Using the Key Migration Tool (KMTool)
- Test Appliance Funcationality
- Collect KeyAppliance Health Data (SAHC.sh)
- Fix Data Inconsistency in DB
- Back
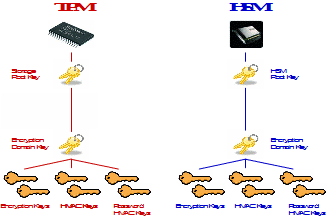
SAKA uses a hardware-based cryptographic module to protect all cryptographic keys generated and used within the appliance. SAKA uses either a Trusted Platform Module (TPM) or a Hardware Security Module (HSM). While there are many differences between these two types of devices, they deliver similar benefits for some functions. SAKA leverages those specific functions and can, thus, deliver identical cryptographic services regardless of the type of cryptographic hardware used in the appliance.
Keys used within SAKA are organized into hierarchies, as shown here:
Copyright (c) 2001-2025 StrongAuth, Inc. (dba StrongKey) All Rights Reserved
