To submit a batch operation to the appliance, the requester—who may be a human being or an application—must submit the XML input file and a web service request to the appliance. The last section discussed how to transfer the input XML file to the appliance.
Submitting the web service request to the appliance is no different from submitting any other SAKA web service request: it requires four parameters, as follows:
|
DID |
The unique encryption domain identifier. |
|
username |
The username (service credential) within the encryption domain with the authorization to call this web service. The credential requires the Key Component Operator (KMO) privilege. |
|
password |
The password of the username to authenticate the credential of the requester. |
|
filename |
The filename of the XML input file that was transferred to the appliance before the web service request is made. The filename must not include any path qualifiers—just the name of the file. |
An example of submitting a batch encryption request using the sakaclient.jar client program is shown below:
java -jar sakaclient.jar https://demo2.strongauth.com:8181 1 encryptonly Abcd1234! BE 1-ABCD-20100920T163300.xml
Upon successfully sending the batch web service request, the sakaclient.jar program displays the following output:
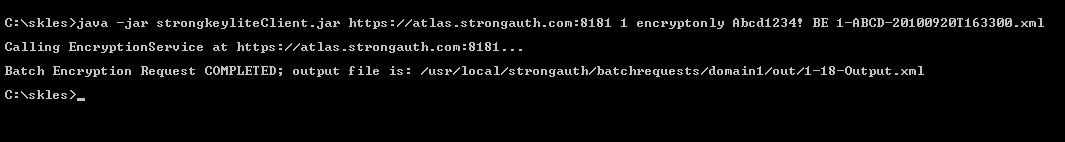
The output file produced from the batch execution has the following name format: the domain identifier, followed by the unique batch request ID assigned to this job, followed by -Output.xml. The example above indicates that this was the 18th batch request job submitted to domain ID 1, hence the output file has a name of 1-18-Output.xml.
Using SFTP (or NFS or SMB if it is configured), the requester can now pick up the processed output file.
 NOTE: While the appliance will automatically delete input XML files for encryption and search operations (it keeps the input XML files for the decrypt and delete operations since they do not have any sensitive data in them), the output files MUST be deleted after transferring them if they were submitted for any operation other than the Delete operation. This is because all other operations result in output files that will have the unencrypted sensitive data in them. Not transferring and deleting these files immediately after the web service call has completed will increase the risk of plaintext being exposed. NOTE: While the appliance will automatically delete input XML files for encryption and search operations (it keeps the input XML files for the decrypt and delete operations since they do not have any sensitive data in them), the output files MUST be deleted after transferring them if they were submitted for any operation other than the Delete operation. This is because all other operations result in output files that will have the unencrypted sensitive data in them. Not transferring and deleting these files immediately after the web service call has completed will increase the risk of plaintext being exposed. |
All the other batch operations use the identical four parameters: DID, username, password, and input filename. The only difference is inside the XML input file which identifies the cryptographic operation that must be performed.
