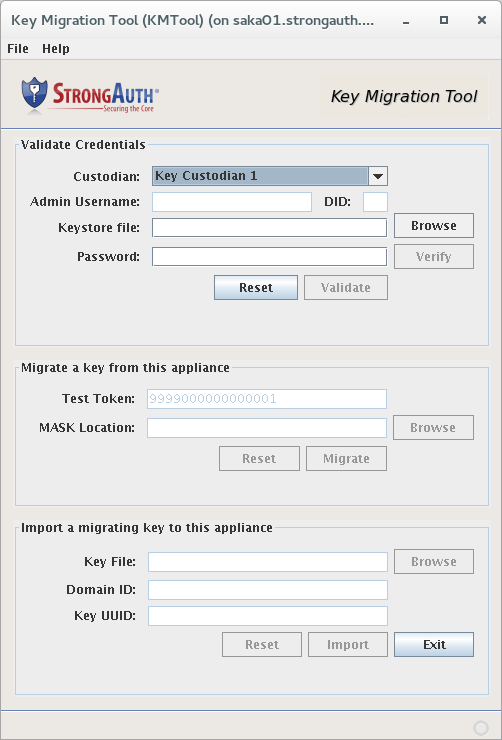
KMTool enforces strict controls for the migration of an EDK. All three Key Custodians (KCs) and the Domain Administrator (DA) must provide their credentials to KMTool before an EDK can be exported from or imported to a SAKA.
Additionally, the design of KMTool requires it to be executed locally on the SAKA server. This means that the keystores for the KCs and DA must be accessible to the file system of the SAKA running KMTool. This can be done either by having all KCs and the DA physically available at the location of the SAKA or by copying the KC and DA keystore files over the network onto the SAKA server temporarily. Before copying keystores from a KC keystore, be sure to consult your company's security policy and get the proper approvals.
Besides the security requirement of running KMTool, the Migration Authority Storage Key (MASK) of the SAKA receiving the migrated EDK must be available. This file is created during the Secondary Setup Wizard process, which must be performed prior to using KMTool. Finally, the appliances involved in the migration must have already been activated using the Key Custodian SetPIN Tool.
If you are exporting a migration key, start KMTool on saka01—any SAKA that has the EDK. If you are importing a migration key, start KMTool on saka02—the SAKA that will be receiving the EDK. Execute the /usr/local/strongauth/bin/KMTool.sh shell script from a terminal window. This will display the following window: