This section assumes that the HSM has already been pared for accepting a sensitive key material by being cleared and reloaded.
Working from a clean HSM, there are two primary steps to restore an HSM to production readiness. The first step is to load the MBK on the HSM from MBK smart card backups. After the MBK is loaded, then encrypted backups can be loaded into the HSM.
- Login as "strongauth" user
- Run the tool:
shell> java -jar /usr/local/bin/cat.jar
- If the device list is empty, add the ‘/dev/cs2.0’ as a device and click ‘OK’.
- Login to the tool by clicking on the ‘Login/Logoff’ button and selecting the ADMIN user. Use the key file located under
'/usr/local/strongauth/strongkeylite/etc/ADMIN.key'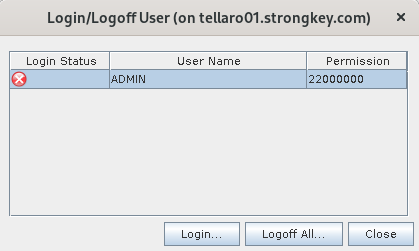
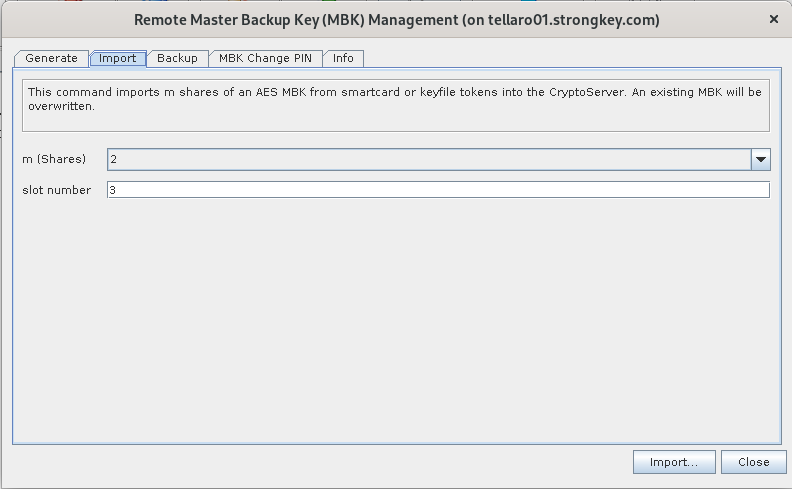
- Import the Master Backup Key that were created on the SmartCards. To do so, click on the ‘Manage MBK’ button
-
Change to the Import tab.
-
Click Import. Share Import window allows importing the MBK backup from a choice between smart cards or keyfiles. Leave the selection as MBK Smartcard Token and click OK.
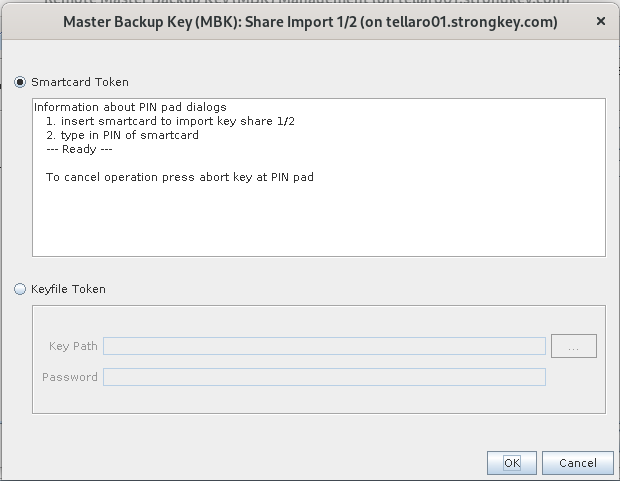
-
Use any 'm' MBK smart cards from the 'n' MBK cards originally created. The chosen MBK smart card holder must then follow directions on the smart card reader.
-
Once the first one is done with this share, it will move on to the second share. Import the second share to finish the process.
-
After finishing the MBK import, Close the Remote Master Backup (MBK) Management window. Open it again with the menu option Manage MBK. It must be closed and opened again to refresh the information in the Info tab (it is not automatically refreshed after generating an MBK).
-
Now select the Info tab:
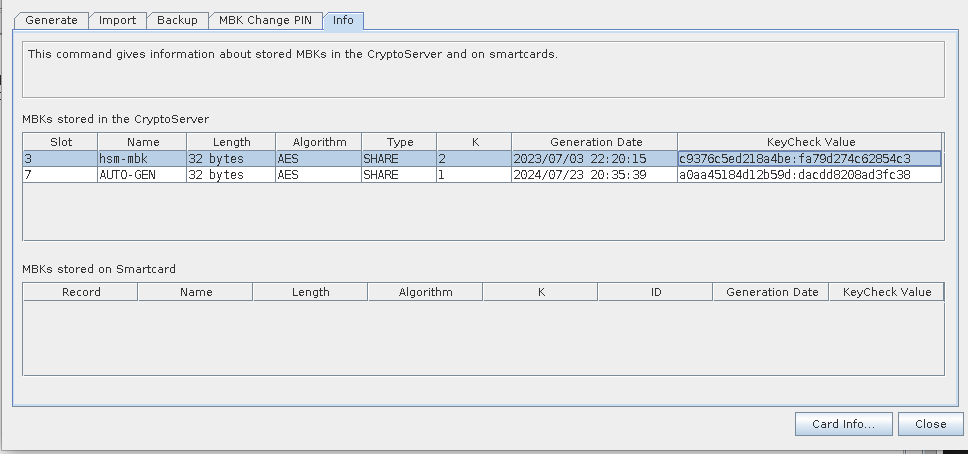
-
The Info tab shows details about this MBK. Verify the MBK KeyCheck Value is the same as when it was first generated in the backup.
