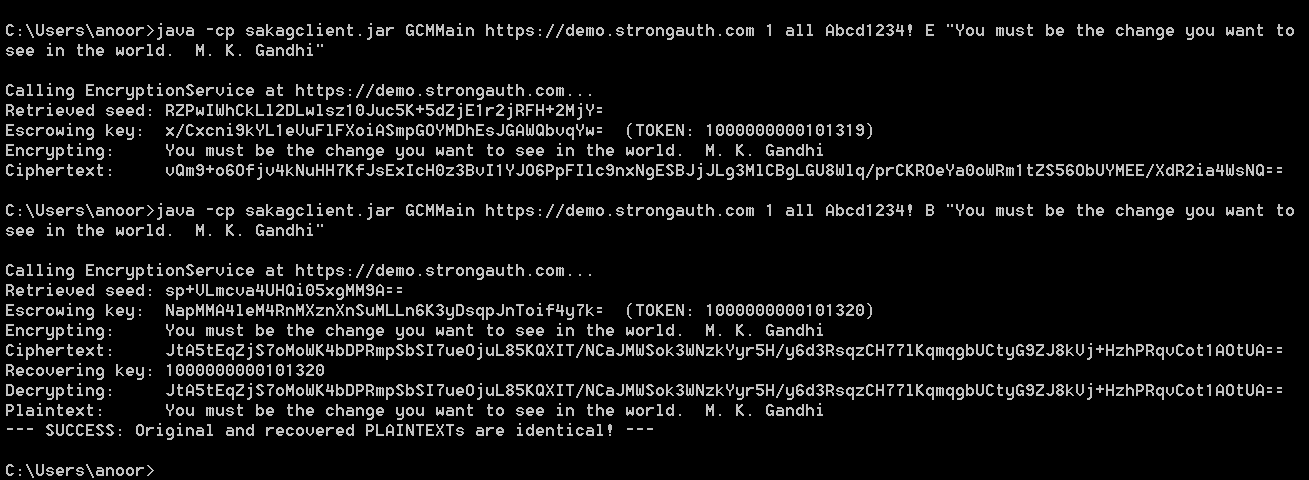
To test the GCM of authenticated encryption, type in the following command:
java -cp sakagclient.jar GCMMain https://demo.strongkey.com 1 all Abcd1234! E “You must be the change you want to see in the world. M. K. Gandhi”
java -cp sakagclient.jar GCMMain https://demo.strongkey.com 1 all Abcd1234! E “You must be the change you want to see in the world. M. K. Gandhi”
This is, essentially, asking the sakagclient to encrypt the string specified on the command line using the GCM mode of operation. The result of this execution is shown in the top half of the figure below.
In this execution, sakagclient first calls KAM to retrieve some entropy from the TRNG on the SAKA (shown in the retrieved seed line). It then generates a new AES key, escrows it on the KAM and gets a token (1000000000101319). Using the last 96 bits of the token for the Additional Authenticated Data (AAD), sakagclient then encrypts the supplied string in the GCM mode of operation to display the resulting ciphertext.
In the bottom half of the following figure, the same string is encrypted and decrypted by specifying the B (both) option. It performs the same operations as for the encrypt operation, but goes on to recover the original cryptographic key by recovering it from KAM, decrypting the ciphertext and comparing the original plaintext with the decrypted value.