To encrypt a test string, type in the following commands separately. In this example the URL is https://demo.strongkey.com, the domain ID is the numeral 1, the username is all and the password is Abcd1234!. The string to be encrypted is within double quotes:
java -jar sakagclient.jar https://demo.strongkey.com 1 all Abcd1234! E “You must be the change you want to see in the world. M. K. Gandhi”
java -jar sakagclient.jar https://demo.strongkey.com 1 all Abcd1234! B “You must be the change you want to see in the world. M. K. Gandhi”
java -jar sakagclient.jar https://demo.strongkey.com 1 all Abcd1234! B “You must be the change you want to see in the world. M. K. Gandhi”
The top half of the window pictured below shows the sequence of activities performed by sakagclient: a new AES encryption key was generated by the client (shown as a Base64-encoded string on the first line) and escrowed on the KAM, which returned the token 1000000000101315. Using the token as the initialization vector (IV) for the CBC mode of operation, sakagclient encrypts the string within double quotes and displays the Base64-encoded ciphertext on the last line of the output.
The bottom half of the window pictured below shows a variation of the same command, but this time the command has specified the B option, which encrypts the supplied string, then immediately decrypts the ciphertext in the same operation and compares the decrypted plaintext with the original to determine if they are the same.
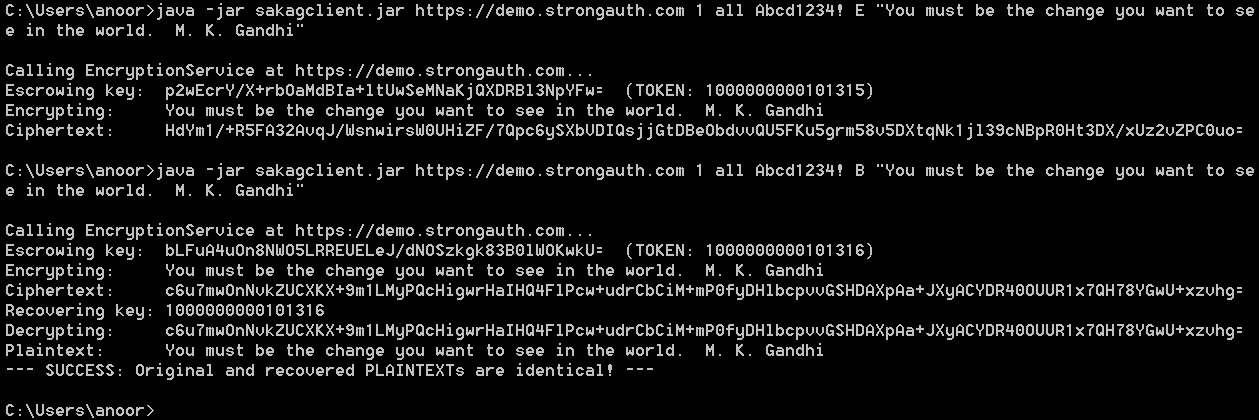
The second command also generates a new AES key and escrows it—resulting in a new token 1000000000101316—then recovers the escrowed key from the KAM and decrypts the ciphertext to compare with the original. As the output shows, the original and decrypted plaintext are identical.
The KAM has the ability to escrow cryptographic keys in this manner—TDES, AES, RSA, ECDSA—almost any cryptographic (or binary) object that can be Base64-encoded to a UTF-8 string of length less than 10,000 characters can be encrypted and stored on the SAKA server as a secure vault. SAKA has been successfully used to store more than 50 million objects in production use at customer sites.
An error message resembling the following implies the SAKA server's TLS certificate has not imported successfully into the JVM.
Exception in thread "main" javax.xml.ws.WebServiceException: Failed to access the WSDL at: https://demo.strongauth.com/strongkeyliteWAR/EncryptionService?wsdl. It failed with: sun.security.validator.ValidatorException: PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target. at com.sun.xml.internal.ws.wsdl.parser.RuntimeWSDLParser.tryWithMex (RuntimeWSDLParser.java:151) at com.sun.xml.internal.ws.wsdl.parser.RuntimeWSDLParser.parse (RuntimeWSDLParser.java:133) at com.sun.xml.internal.ws.client.WSServiceDelegate.parseWSDL (WSServiceDelegate.java:254) at com.sun.xml.internal.ws.client.WSServiceDelegate.<init> (WSServiceDelegate.java:217) at com.sun.xml.internal.ws.client.WSServiceDelegate.<init> (WSServiceDelegate.java:165) at com.sun.xml.internal.ws.spi.ProviderImpl.createServiceDelegate (ProviderImpl.java:93) at javax.xml.ws.Service.<init> (Service.java:56) at com.strongauth.strongkeylite.web.EncryptionService.<init> (EncryptionService.java:79) at strongkyeliteClient.Main.main (Main.java:109)
If the certificate seems to have successfully imported into the JVM, and can see it when listed within KeyTool, then the Command Tool is likely pointing to a different JVM in its Path setting. Make sure the Command Tool is using the JVM with the imported certificates in its cacerts file. Either change the Path setting permanently through the Control Panel, or change it temporarily in the Command Tool itself.
Alternatively, call the correct JVM by specifying the full pathname of the Java executable without changing the Path.
An error resembling the following implies that a JAR library—bcprov-jdk15on-1.54.jar—is not in the lib subdirectory where sakagclient exists.
Make sure there is a subdirectory called lib in the same folder where the sakagclient.jar file exists, and that BouncyCastle JCE Provider 1.54 exists in the lib subdirectory. Then attempt the command again.
Exception in thread "main" java.lang.NoClassDefFoundError: org/bouncycastle/util/encoders/Base64
at GCMMain.decryptText(GCMMain.java:324)
at GCMMain.main(GCMMain.java:237)
Caused by: java.lang.ClassNotFoundException: org.bouncycastle.util.encoders.Base64
at java.net.URLClassLoader.findClass(URLClassLoader.java:381)
at java.lang.ClassLoader.loadClass(ClassLoader.java:424)
at sun.misc.Launcher$AppClassLoader.loadClass(Launcher.java:331)
at java.lang.ClassLoader.loadClass(ClassLoader.java:357)
... 2 more