Before a DA can perform any function with the SAKA server, they must connect to the server; the DA must have the USB flash drive with their digital certificate (in the BCFKS file) on it, containing their PrivateKey.
When the DA attempts to connect to the SAKA server with the DACTool, the tool requests a nonce—a random number used only once—anonymously. The server generates a random nonce from its True Random Number Generator (TRNG) and sends it to DACTool. DACTool, upon receiving it, prompts the DA for the password to the BCFKS file. Upon getting the correct password, DACTool uses the PrivateKey to digitally sign the nonce before sending the connection request to the SAKA server. If the digital signature on the nonce is verified correctly by the server and the random nonce is accurate, the SAKA server establishes a connection. The DA may now perform administrations commands on the SAKA server.
Whether a DACTool command succeeds or fails, SAKA always sends a new randomly generated nonce in the response. Every new administration command sent by the DACTool must include the new nonce—digitally signed—to the SAKA server. The signed nonce is always verified before the command is executed.
To open the Systems panel, click Systems → View Systems on the menu or click the Systems icon on the Main Panel. The following dialog opens:
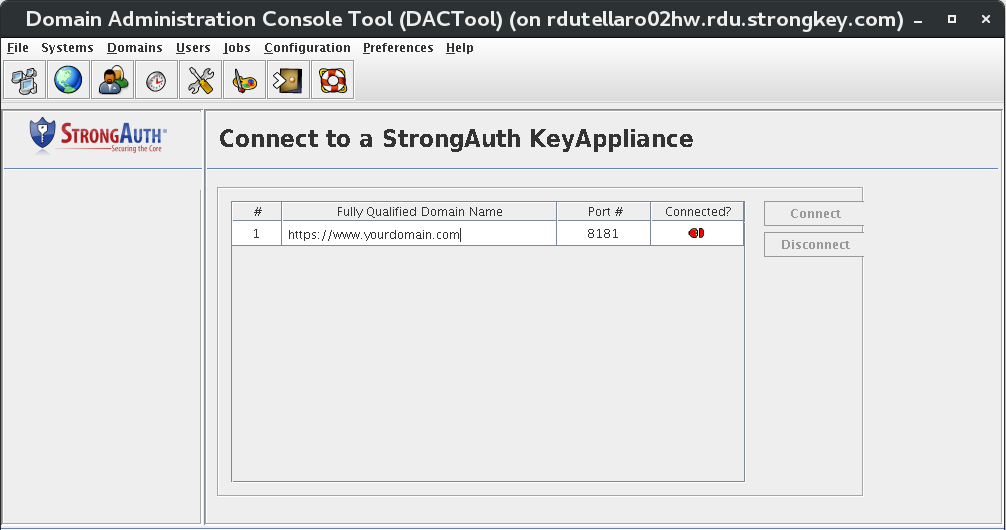
The panel shows a table with all configured appliances in a table. The table shows the FQDN of the server, the port number where the Administration Service is listening, and an icon—either in red or green color—to indicate if the DACTool is currently connected to SAKA or not. In the above figure, it shows one SAKA server listening on port 8181—the same port where the Encryption Service is typically accessible—and red connection icons indicating that the DACTool is not connected to any one of them.
There are two buttons—Connect and Disconnect—that are initially disabled. Upon selecting a specific SAKA server, one of the two buttons will become enabled. If DACTool does not have a connection to a SAKA server, it will enable the Connect button; if DACTool is already connected to it—indicated by a green connection icon—the Disconnect button becomes enabled.
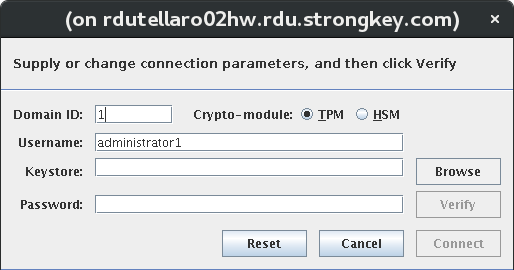
When the Connect button is selected, the tool displays the Connection Parameters panel, shown below. If the DA has saved any preferences earlier, they will be displayed here; otherwise, the application's default values will be displayed. The DA may specify values in the Connection Parameters panel before making the connection.
|
Domain ID |
The unique numeric identifier of the default encryption domain to which the DA will connect when using DACTool. |
|
Crypto-module |
This radio button tells the DACTool which cryptographic hardware module is used on the appliance. This is necessary for DACTool to use the appropriate cryptographic algorithms when digitally signing the authorization nonce (number used once) for verification by the appliance before executing the command. The two choices for this field are:
Select the option that matches the cryptographic hardware module on your SAKA server. TPM is the default cryptographic module on most SAKA installations. |
|
Username |
The username of the domain administrator within the encryption domain to which they will connect. |
|
Keystore |
The location of your BCFKS keystore file where your cryptographic keys and digital certificate are stored. Without this keystore, it is impossible to connect to the SAKA server's administration service. |
|
Password |
The BCFKS keystore file is encrypted using Password-Based Encryption (PBE). Passwords are never stored or saved on the system. |
|
Verify |
Upon typing the password to the BCFKS keystore, the Verify button becomes enabled. Before DACTool establishes a connection with the SAKA server, verify the correct password has been used to access the PrivateKey in the BCFKS file. Without the right password, digitally signing the nonce becomes impossible. If the password is incorrect, the panel will display an appropriate message and the Connect button remains disabled. However, if the password correctly decrypts the BCFKS file, the Connect button becomes enabled. |
|
Reset |
Resets the panel values to the defaults. |
|
Cancel |
Cancels the connection to the SAKA host and returns to the Systems panel. |
|
Connect |
This button becomes enabled only when the BCFKS keystore password is verified. Upon selecting it, DACTool retrieves the current nonce it possesses, digitally signs it with the PrivateKey from the BCFKS keystore, and sends a connection request to the SAKA server. |
After typing the password to the keystore, click Verify.
 NOTE:If the password is incorrect, a message appears, stating, “Password does not verify keystore.” Make changes to the password and click Verify again. NOTE:If the password is incorrect, a message appears, stating, “Password does not verify keystore.” Make changes to the password and click Verify again. |
Upon supplying the correct values in the Connection Parameters panel and confirming the keystore password is correct, click the Connect button. DACTool attempts to connect to the selected SAKA server and provides one of two possible responses.
If the SAKA services are not running, or if they are but the Key Custodians of the SAKA have not activated the cryptographic hardware module on the server since the server was restarted, the following error message displays on the status bar of DACTool:
Could not get a nonce from server—the SAKA service may not be running or the Key Custodians may not have activated the crypto-module.
If such an error message is displayed, the DA cannot do anything with the SAKA server until the services have been started and the Key Custodians activate the cryptographic hardware module. (See Chapter 10 for more details).
If the services are running and the Key Custodians have activated the cryptographic module, the connection icon will turn green and a message displays, “Successfully connected to the SAKA server.” The Disconnect button also becomes enabled.
All administrative tasks on this encryption domain on the SAKA are now available until it the Disconnect button is clicked or DACTool is closed.
