Strongkey KeyAppliance comes with the pingsaka.sh utility to test and confirm the functionality of the KeyAppliance. It can also be used to check SAKA version installed on the appliance.
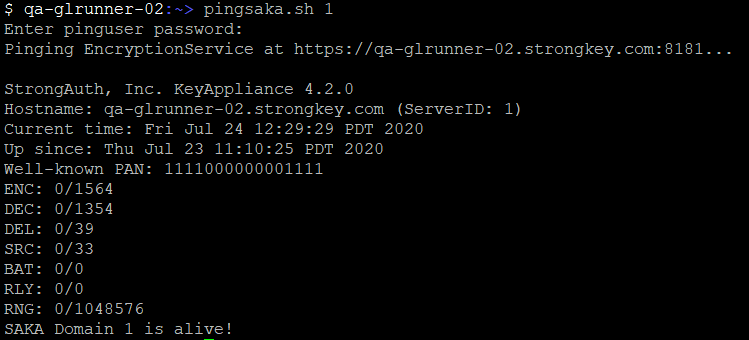
The first line, the well-known PAN, is a constant value. It should never change whenever you send a request to the same server for the same domain ID. If you send the request to other servers it will change, and it could possibly change if you send the ping to a different domain on the same server, that would depend on how each domain as configured.
Each of the following lines will most certainly change over time. Each of those line describes an operation the appliance supports and on that line the first number is how many times that type of request has occurred since the last time the server rebooted and the second number is the lifetime total number of requests of that type.
- ENC - Encryption Request
- DEC - Decryption Request
- DEL - Deletion Request
- SRC - Search Request
- BAT - Batch Request
- RLY - Relay Request
|
|
The last line for RNG is different. The appliance can be configured to return true random numbers from the TPM and a buffer of those can be stored in memory to make that operation faster. The 0 describes how many bytes of random numbers are stored and the 1048576 is how many total bytes can be stored. Unless you were to run on the property for this buffer, these numbers would be the same every time you ping.

 NOTE: The numbers for ENC requests only gets updated when the new token has been created. If you send the encryption request for plaintext value for which the token already exist and returns that existing token, it would not add to the count. The numbers for DEC requests will not get updated for the pingsaka.sh script execution as well.
NOTE: The numbers for ENC requests only gets updated when the new token has been created. If you send the encryption request for plaintext value for which the token already exist and returns that existing token, it would not add to the count. The numbers for DEC requests will not get updated for the pingsaka.sh script execution as well.