The second panel of KMTool is the Migrate a key from this appliance panel. This panel allows you to specify a MASK file from saka02 and create migration keyfile.
-
Complete the fields as described below.
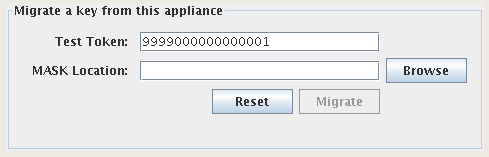
Test Token
A unique Pseudo-Number (Token) created on the Primary appliance, to be used for a decryption test on the new appliance. The standard “well-known token” is 9999000000000001 and was created during the installation wizard. This value is currently not used during the key migration process and can be safely left as default.
Mask Location
Location of the MASK file of the saka02 appliance. In a production environment, this file is on the black flash drive but can also be found on saka02 in the
/usr/local/strongauth/strongkeylite/etc directory. -
When finished, click Migrate. This action generates a migration keyfile (in the same directory as saka02's MASK file) with a filename that has the following format:
<source-appliance-FQDN>-<target-appliance-FQDN>-<domain Id>-migkey.xml
...where FQDN is the fully qualified domain name of the appliance. In this example, the filename is:saka01.strongauth.com-saka02.strongauth.com-1-migkey.xml
-
If the migration key is generated successfully, KMTool will produce the following message: “Migrated Encryption Domain #1's master-key to [target-appliance-FQDN].”
 NOTE: Additional EDKs can be migrated from other domains before closing KMTool. To migrate another EDK, validate the DA from the extra domain (don't forget to change the DIDfield). After validating the domain, click Migrate again to generate another migration key for this extra domain. This process can be repeated for each other domain. NOTE: Additional EDKs can be migrated from other domains before closing KMTool. To migrate another EDK, validate the DA from the extra domain (don't forget to change the DIDfield). After validating the domain, click Migrate again to generate another migration key for this extra domain. This process can be repeated for each other domain. |
