The SAKA is capable of storing externally generated ANSI X9.24-1 Keys for use in the various DUKPT operations supported by the CardCrypto Service. These keys can be stored on the SAKA in two ways:
-
Through the loading of 2‒3 separate key components into SAKA after which the SAKA can assemble the key by combining the components
-
The key can be submitted to SAKA in an encrypted form if the wrapping key has already been loaded into SAKA
Once the plaintext key has been assembled or unwrapped, the key is reencrypted by the current data encryption key and is assigned a token number which is returned to the user. The key's token must be submitted to the SAKA any time the key is needed by a web service operation.
The following diagram describes the process of storing a key from key components:
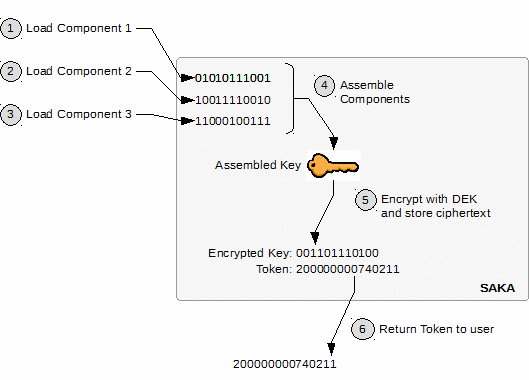
In Steps 1‒3 of the above diagram, up to three key components are submitted to the appliance.
In Step 4, the components are combined into the Assembled Key—either a Base Derivation Key (BDK) or Local Terminal Master Key (LTMK).
In Step 5, the assembled key is encrypted using the current data encryption key and its ciphertext is stored in the database. At this point, the assembled key bytes are discarded.
A token reference for this key is assigned and returned to the user in Step 6.
The following diagram describes storing a key wrapped by another stored key:
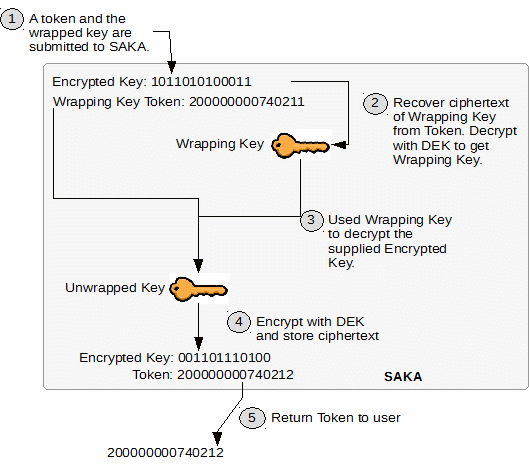
In Step 1, the user submits a token which identifies a previously stored wrapping key and the encrypted key to be stored.
In Step 2, SAKA recovers the ciphertext of the wrapping key from the token and uses the data encryption key to decrypt the Wrapping Key.
In Step 3, the Wrapping Key is used to decrypt the encrypted key ciphertext, resulting in the Unwrapped Key—either a Terminal Master Key (TMK) or a Terminal PIN Key (TPK).
In Step 4, the Unwrapped Key is encrypted using the current data encryption key and its ciphertext is stored in the database. At this point, the unwrapped key bytes and wrapping key bytes are discarded.
A token reference for this key is assigned and returned to the user in Step 5.
In this manner, a hierarchy of keys can be stored in SAKA to be used for DUKPT operations or PIN Block decryption and encryption.
