For cryptographic services to be available on SAKA, the cryptographic hardware module on the appliance must be activated. The cryptographic module—either the Trusted Platform Module (on the Model-T) or the Hardware Security Module (on the Model-H)—holds the “root” key of the key hierarchy that protects all cryptographic keys on the appliance. However, the hardware module can only be activated by Key Custodians (KCs) with their Personal Identification Numbers (PINs)—which they established during the installation of the appliances. Only when the hardware module is activated, does the “root” key become available, which in turn, enables cryptographic services to become available to business applications.
 NOTE: SAKA security is entirely predicated on the “root” key. However, on the Model-T, the Storage Root Key (SRK) cannot leave the hardware module—this is part of the design specification for the TPM, as specified by the Trusted Computing Group (TCG). Once created upon initialization, the SRK can only be activated for use or destroyed during re-initialization. On the Model-H, the “root” key is generated inside the HSM, and can leave the HSM only under the protection of another encryption key in a controlled process. NOTE: SAKA security is entirely predicated on the “root” key. However, on the Model-T, the Storage Root Key (SRK) cannot leave the hardware module—this is part of the design specification for the TPM, as specified by the Trusted Computing Group (TCG). Once created upon initialization, the SRK can only be activated for use or destroyed during re-initialization. On the Model-H, the “root” key is generated inside the HSM, and can leave the HSM only under the protection of another encryption key in a controlled process. |
In the event of a restart of the SAKA, since it is unfeasible for KCs to be available in remote server-rooms where the SAKA is typically deployed, SAKA includes a client application—the Key Custodian SetPIN Tool (KCSPTool)—that allows KCs to activate the hardware module from remote locations. All that is required is for the KCs to have a connection to SAKA from their computers and the USB flash drive that contains their credential (which was created when SAKA was initially set up).
While it is recommended that KC connections be controlled through an access-control list of a router or switch to prevent denial-of-service (DoS) attacks, the connection need not be secured for confidentiality since SAKA accepts KC commands and responses only over a secure transport protocol—Transport Layer Security.
The installation process of SAKA instances would have resulted in the KCs being given the KCSPTool on some media they would use to install on their computers. Since the KCSPTool is a Java application, it can run on any platform where a Java Virtual Machine (JVM) is available. It is necessary for the KCs to have a supported version of the JVM on their computer to use the tool. See 3—Architecture for the supported version of the JVM for your appliance.
On a Windows PC, the KCs would use a Command Tool script (a batch file) to start the KCSPTool. On a Linux computer, this would be shell script. The script file can be associated with an icon on the KC's desktop to make it convenient for the KC to use the tool.
 NOTE: It is strongly recommended that KCs never copy their credential file from the USB flash drive to their computer for convenience. While it might be tempting, leaving the file on the computer could leave the file vulnerable as it might be copied off by an attacker, who might then try to determine the KC's PIN by subjecting the file to a dictionary attack or a rainbow table attack. Sites may not only want to enforce this through a company policy, but also through automated tools that delete such credential files when found on the hard disk of a KC's computer. Ultimately, the site must rely on the responsibility of the KC to preserve the security of their credential—policies and automated tools can only go so far. NOTE: It is strongly recommended that KCs never copy their credential file from the USB flash drive to their computer for convenience. While it might be tempting, leaving the file on the computer could leave the file vulnerable as it might be copied off by an attacker, who might then try to determine the KC's PIN by subjecting the file to a dictionary attack or a rainbow table attack. Sites may not only want to enforce this through a company policy, but also through automated tools that delete such credential files when found on the hard disk of a KC's computer. Ultimately, the site must rely on the responsibility of the KC to preserve the security of their credential—policies and automated tools can only go so far. |
When the KCSPTool starts it displays the following screen:
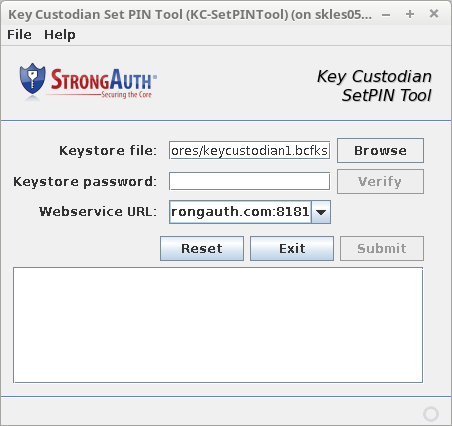
|
Keystore File |
This field identifies the location of the credential file—a Java keystore file containing the KC's 256-bit EC key pair and digital certificate. Activation commands to the appliance must be digitally signed by the KC before they are accepted by SAKA. KCs may use the Browse button to locate the file on the USB flash drive |
|
Keystore Password |
The KC keystore credential is protected with a password selected by the KC at the time SAKA was initially installed. The KC must supply this password in this field to use the EC key to digitally sign the activation command. To prevent mistakes from being transmitted to the server, when the KC types in a password in this field, the Verify button next to it becomes activated. KCs should get into the habit of selecting this button to confirm their password permits access to the credential file before selecting the Submit button. The pain of trouble-shooting invalid commands to the SAKA can be avoided by this simple step. |
|
Webservice URL |
Every SAKA listens to KC commands at a specific URL. This is established at the time of the installation of the SAKA. The KC should specify this URL in this field. SAKA always uses the TLS protocol, so the URL must begin with “https.” |
|
Reset |
Resets all values to the defaults on the tool's panel. |
|
Exit |
Exits the KCSPTool. |
|
Submit |
This button is disabled by default, but if all appropriate fields are filled on the form, the button becomes enabled. Selecting it submits the activation command to the SAKA server. This may take a little while as it must perform the following steps:
Once completed, the KC is provided feedback on whether or not the command succeeded. |
