DISCOVER
A web application demonstrating how to authenticate users to the relying party's site without having the user provide their username - the browser and user's FIDO Authenticator negotiate the capability between them, and make the user experience seamless.
-
Make sure you have imported the two digital certificates into your browser or on the Security Keys, as described above;
-
Start a new Private Browser session;
-
Insert your FIDO Authenticator to a USB Port;
-
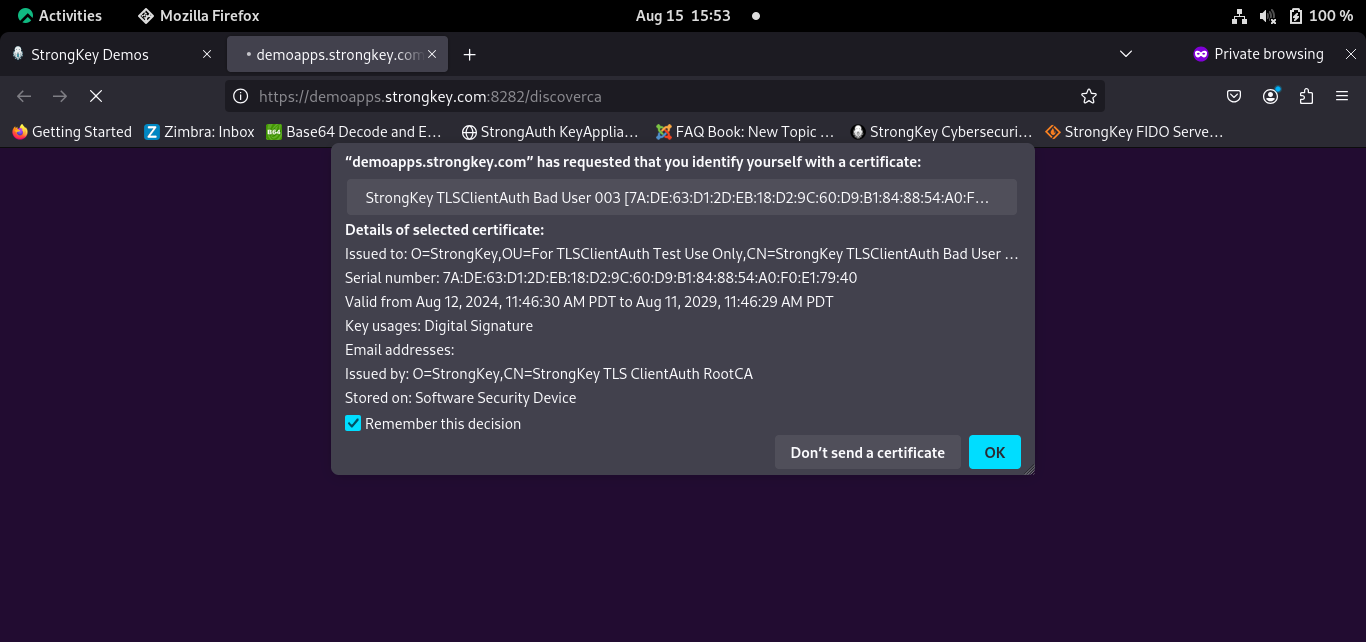
Browse to https://demoapps.strongkey.com:8282/discoverca and follow the steps;
-
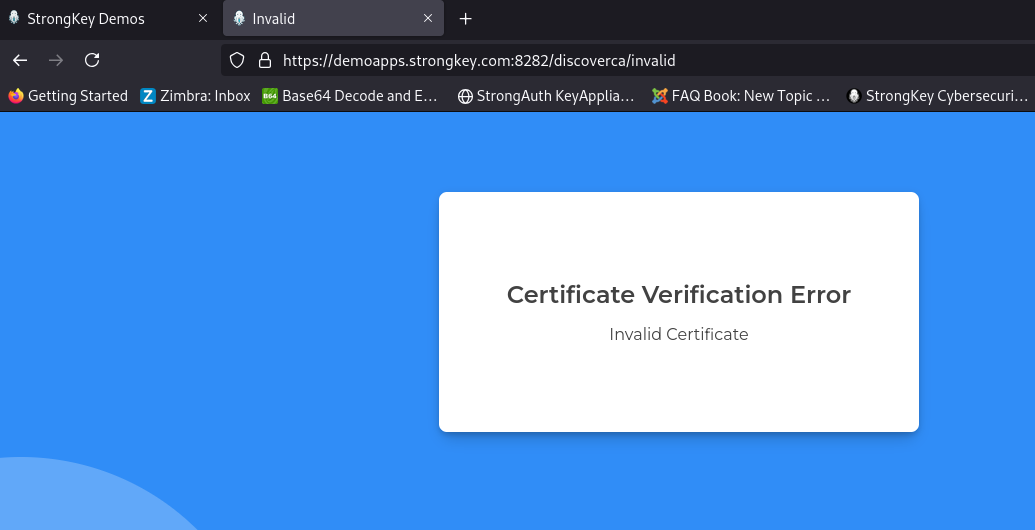
Choose the Bad User digital certificate. Verify that the application refuses to allow you to continue based on the certificate's status;
-
Start a new Private Browser session and visit the URL shown above; if Chrome does not let you start over (because it remembers the use of the revoked certificate), exit the browser, delete the cookies, restart it, and go back to this URL;
-
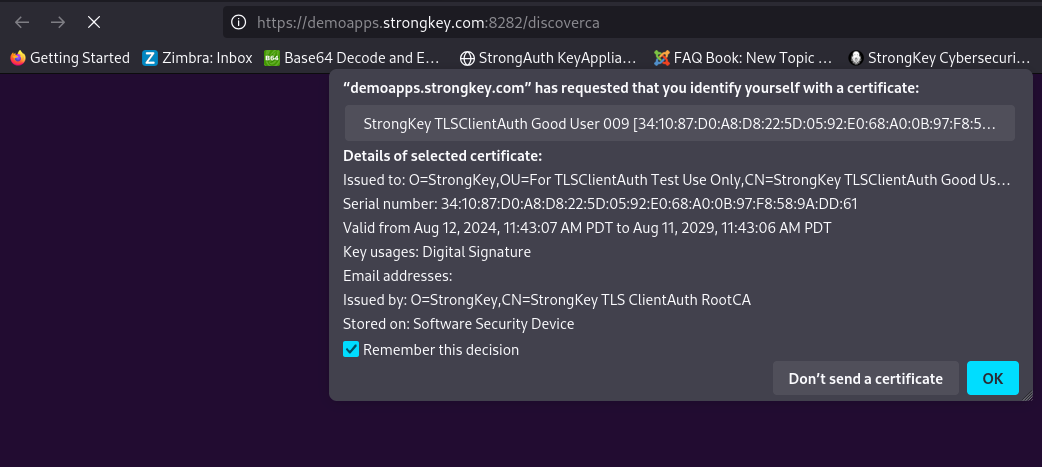
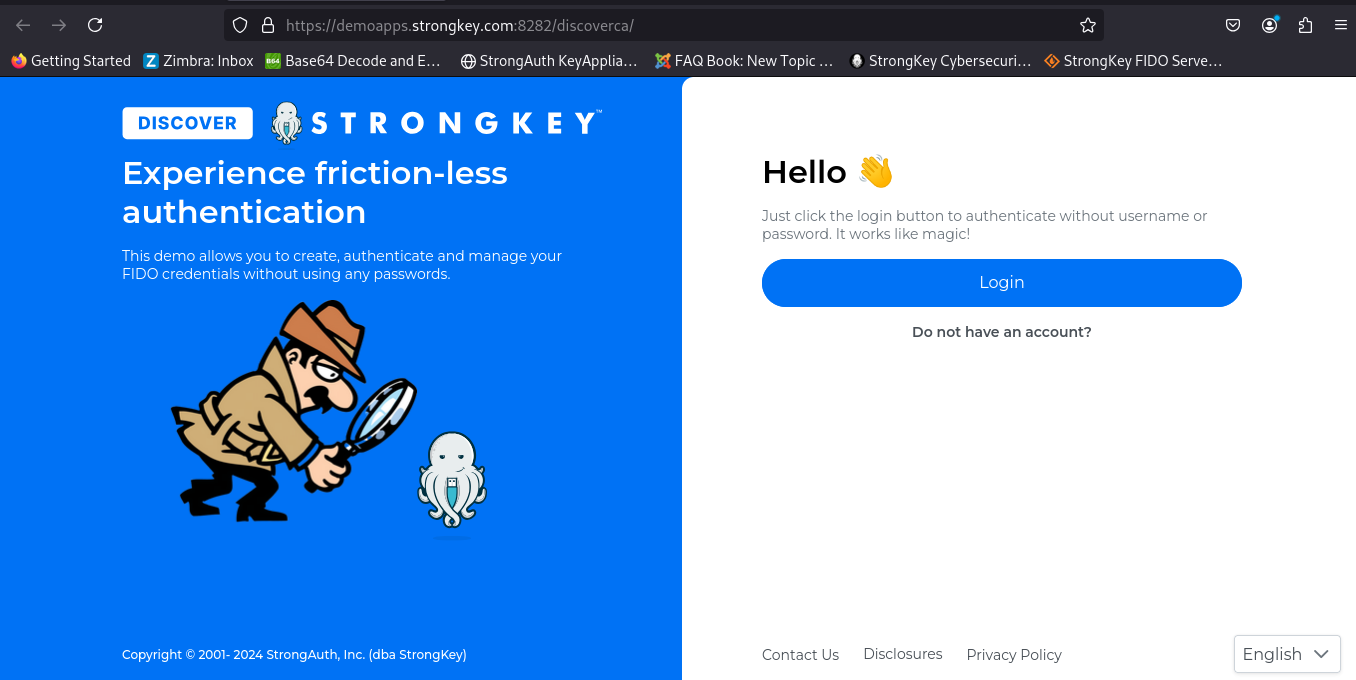
Choose the Good User certificate. Continue on the path the application takes you and register the FIDO Authenticator with the site;
-
Continue to authenticate without putting the username;
-
If successful, FIDO Credential Management page would be displayed.
SKSO
StrongKey Sign-On (SKSO) is a purpose-built web application designed to support the registration and management of FIDO credentials with SKFS, as well as inter-operate with Citrix ADC and Citrix Gateway for single sign-on to Citrix environments using SAML Assertions.
-
Make sure you have imported the two digital certificates into your browser or on the Security Keys, as described above;
-
Start a new Private Browser session;
-
Insert your FIDO Authenticator to a USB Port;
-
Browse to https://demoapps.strongkey.com:8282/sksoca and follow the steps;
-
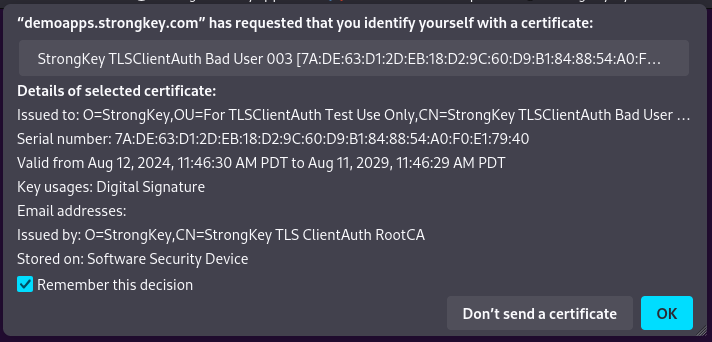
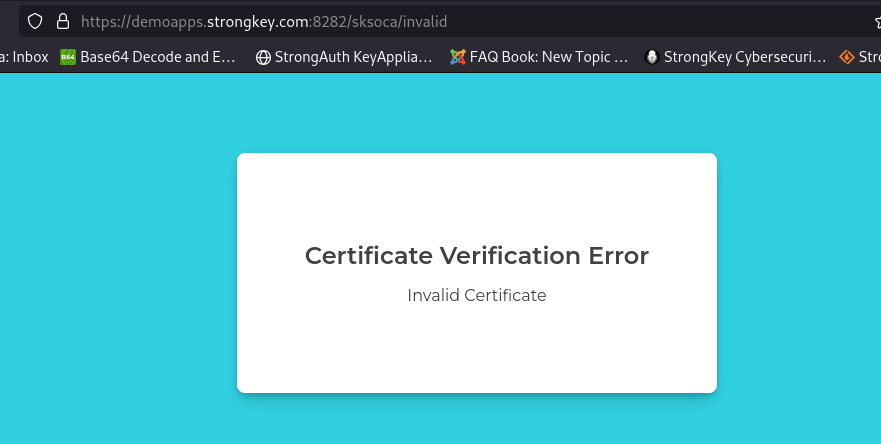
Choose the Bad User digital certificate. Verify that the application refuses to allow you to continue based on the certificate's status;
-
Start a new Private Browser session and visit the URL shown above; if Chrome does not let you start over (because it remembers the use of the revoked certificate), exit the browser, delete the cookies, restart it, and go back to this URL;
-
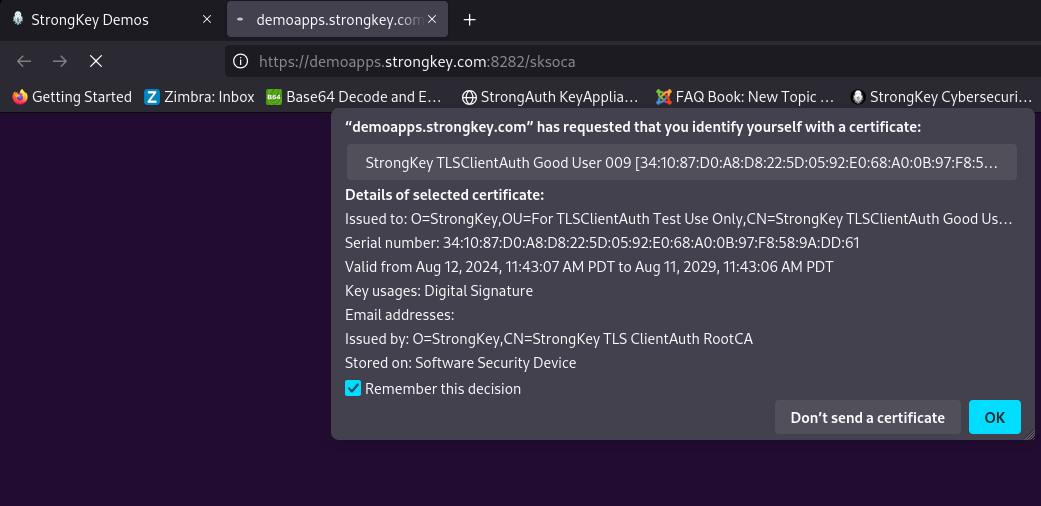
Choose the Good User certificate. Continue on the path the application takes you and register the FIDO Authenticator with the site;

-
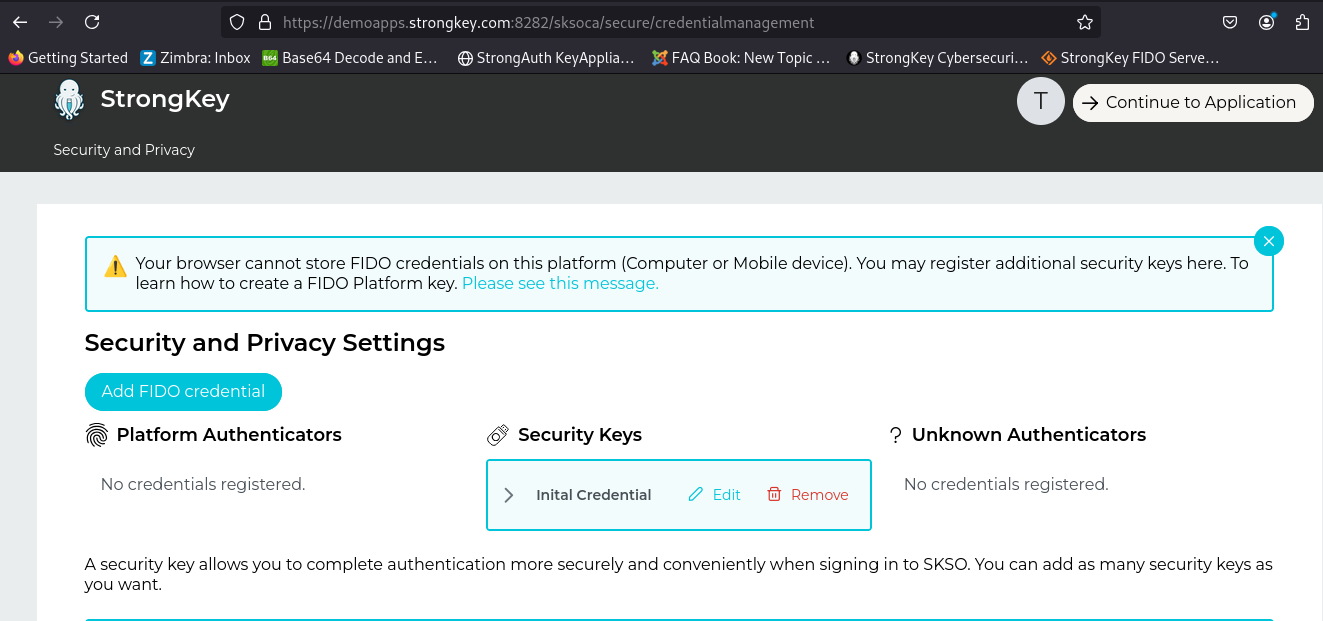
When successful, authenticate with the new credential into the Credential Management Page;
-
Continue to the Citrix Gateway Dashboard.
PKI2FIDO
A basic JAVA application demonstrating how users with X.509 digital certificates can strongly authenticate using TLS ClientAuth and then register a FIDO Security with SKFS.
-
Make sure you have imported the two digital certificates into your browser or on the Security Keys, as described above;
-
Start a new Private Browser session;
-
Insert your FIDO Authenticator to a USB Port;
-
Browse to https://demo5.strongkey.com/pki2fido/angular and follow the steps;
-
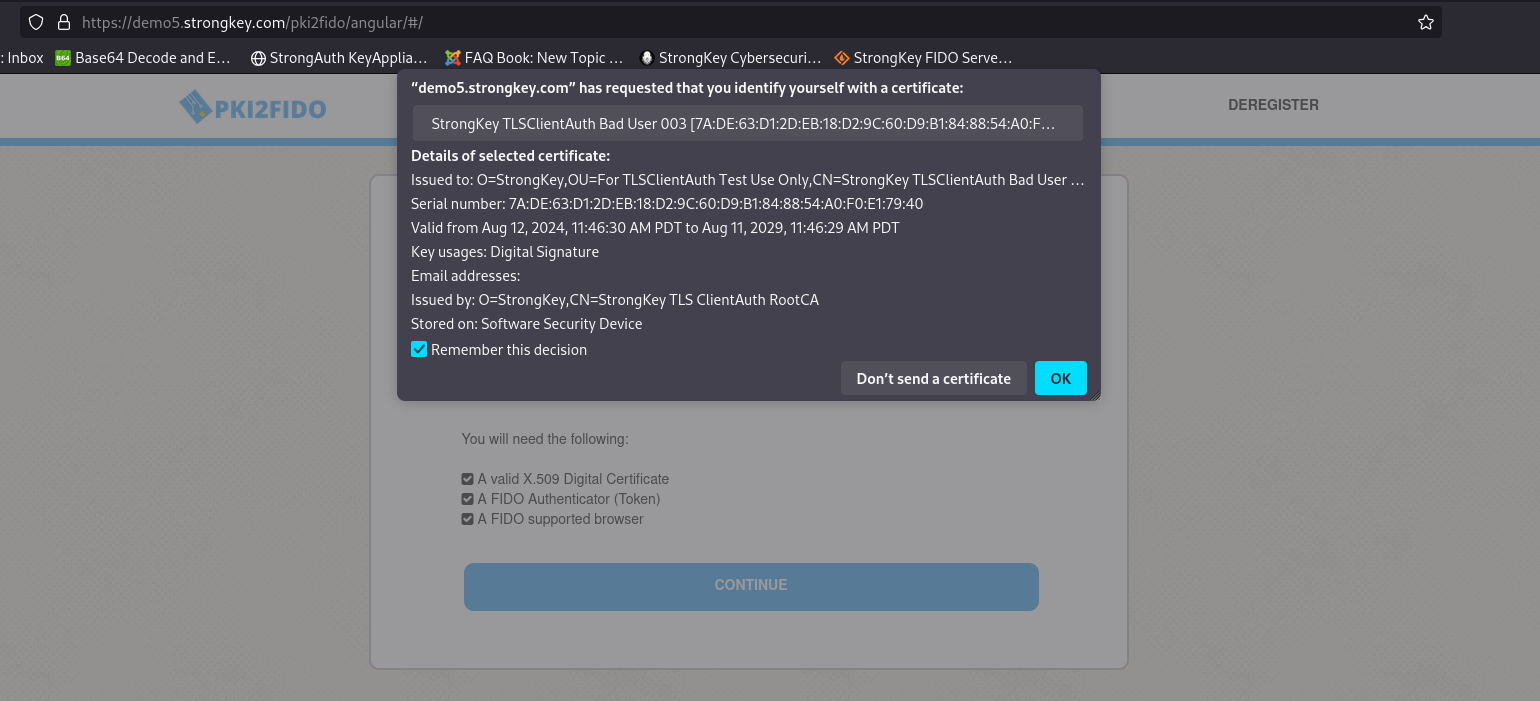
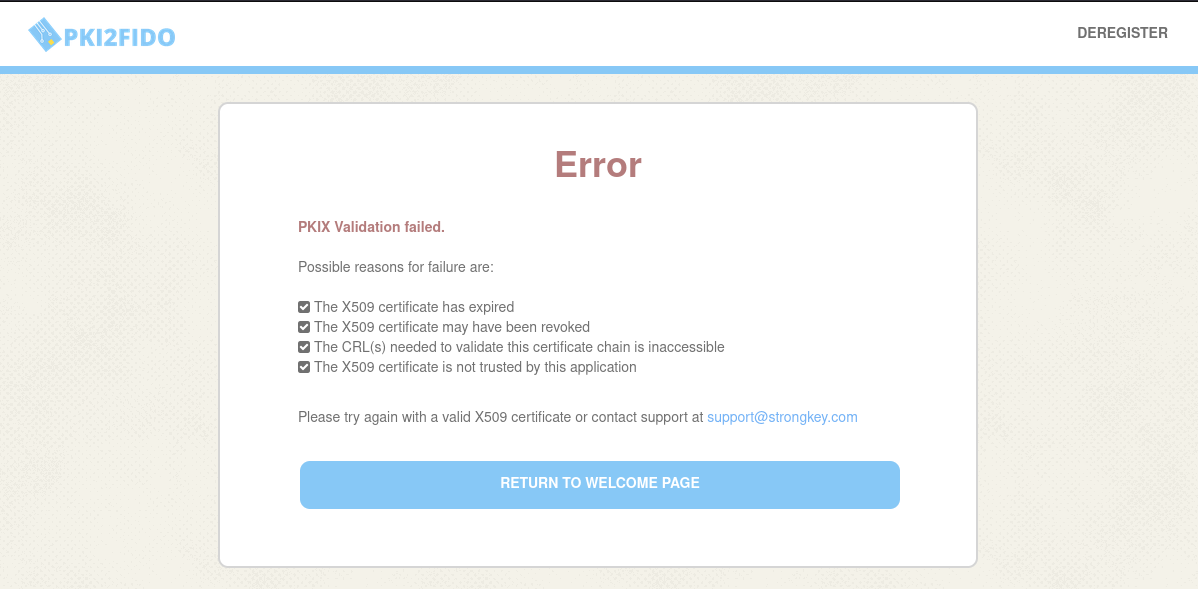
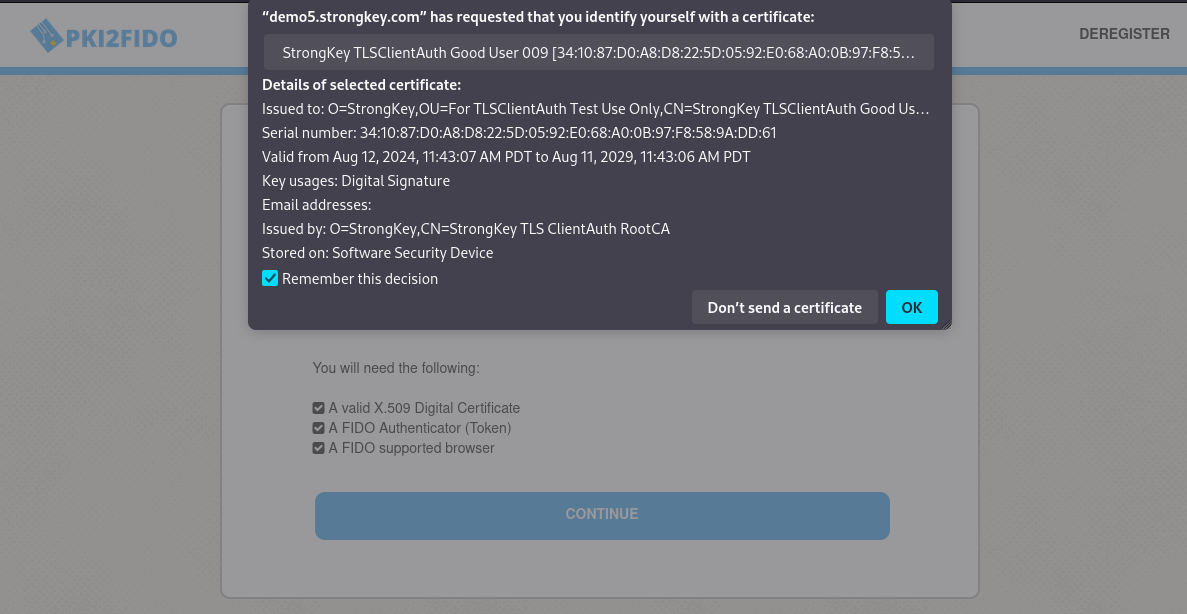
Choose the Bad User digital certificate. Verify that the application refuses to allow you to continue based on the certificate's status;
-
Start a new Private Browser session and visit the URL shown above; if Chrome does not let you start over (because it remembers the use of the revoked certificate), exit the browser, delete the cookies, restart it, and go back to this URL;
-
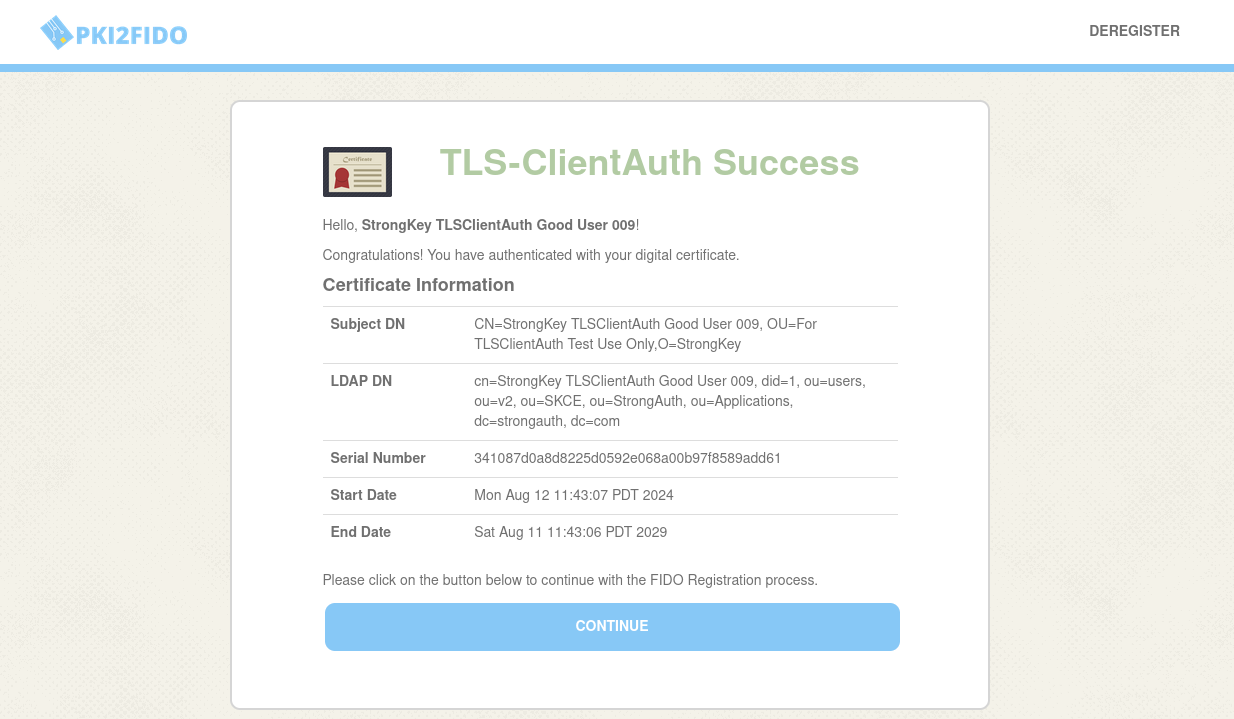
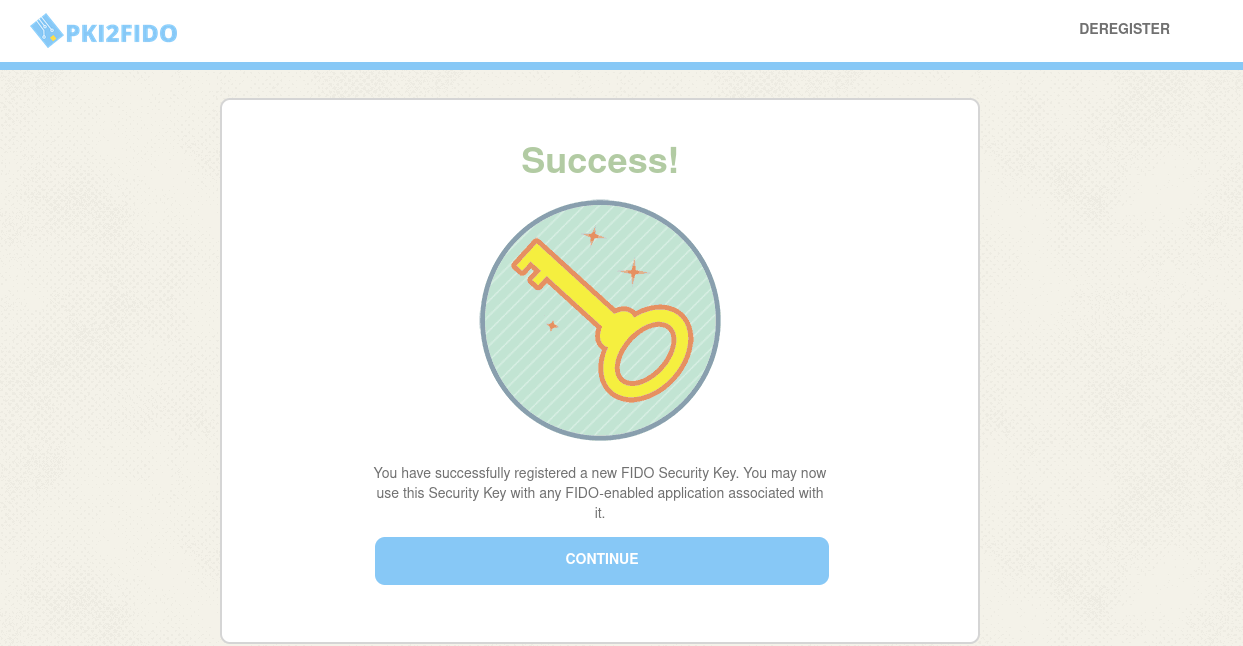
Choose the Good User certificate. Continue on the path the application takes you and register the FIDO Authenticator with the site;
-
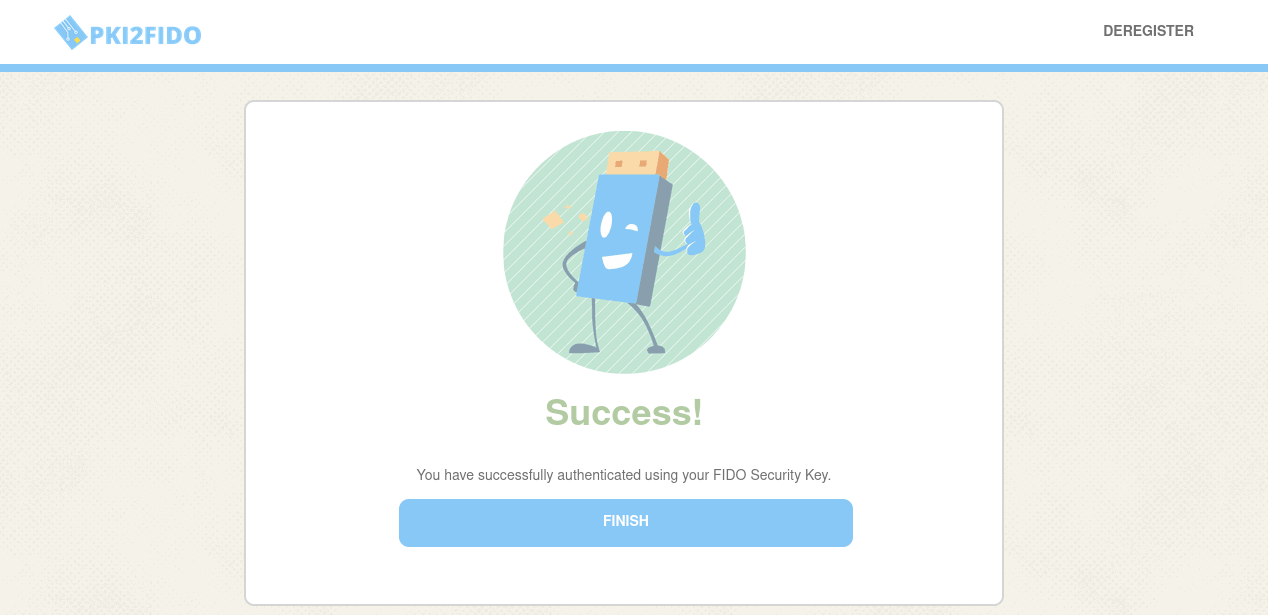
When successful, continue to authenticate with your registered FIDO credential;
-
You can also deregister the FIDO key by clicking the Deregister button.
