To ensure that a specific Security Key is required to prompt for MFA when authenticating to the strongauth account, the Security Key(s) associated with Administrator(s) must be configured within the strongauth account.
This task must be performed by the Linux strongauth account on the Tellaro appliance.
Requiring the strongauth account to require a Security Key to authenticate
-
Login as the strongauth user into the Tellaro appliance, and start a Terminal window.
-
The following command will generate a FIDO key on the Security Key that is inserted on the appliance. It will prompt for a pin if it has been previously configured. This will generate the key for strongauth user for RPID of strongkey.com (replace this with the relevant RPID) and can be used for the entire cluster.
shell> pamu2fcfg -v -o strongkey.com -i strongkey.com -u strongauth > fido-keysSample Output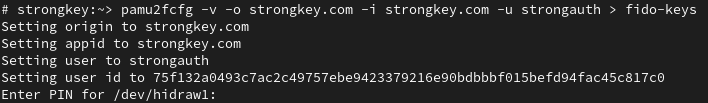
-
In a second terminal, su into the root user.
shell> su - -
Create a folder in which to save all the registered FIDO Keys. Move the resulting file from step 2 into the newly created folder and then log out of root once you are done.
shell> mkdir /etc/strongkey shell> mv /usr/local/strongauth/fido-keys /etc/strongkey/ -
To add additional Security Keys, remove the current Security Key in the machine and plug in a different one. Switch to the first terminal window where the strongauth user is logged in. Repeat step 2 and, after generating the fido-keys file, run the following command to remove the username before the colon ':' and append the result to the already existing fido-keys file.
shell> sed 's/.*:/:/g' fido-keys >> /etc/strongkey/fido-keysRepeat this process for each Security Key you wish to add.
Example of the fido-keys file after adding multiple keys:Notice that the content of the file is one long string with no line breaks. The end of each key is indicated by the string “+presence”, and the colon ‘:’ afterwards indicates the beginning of a new key.
-
Configure PAM to enable the use of Security Keys. There are three files that can be modified based on the use case. These files will have to be modified as the root user.
-
/etc/pam.d/sudo - To enable use of FIDO keys for all sudo commands for strongauth user.
-
/etc/pam.d/login – To enable use of FIDO keys for console login in run level 3.
-
/etc/pam.d/gdm-password – To enable use of FIDO keys for Graphical console login (Run level 5).
-
-
Configure FIDO login for sudo access by making the following modifications to /etc/pam.d/sudo file.
Replace the following line: auth include system-auth with the following block of code (Replace strongkey.com origin with the relevant value) #auth include system-auth auth required pam_env.so auth required pam_faildelay.so delay=2000000 auth [success=1 default=ignore] pam_succeed_if.so user ingroup mfausers auth sufficient pam_unix.so nullok try_first_pass auth [success=2 default=ignore] pam_succeed_if.so user notingroup mfausers auth requisite pam_unix.so nullok try_first_pass auth sufficient pam_u2f.so authfile=/etc/strongkey/fido-keys debug debug_file=/var/log/pamfido.log cue pinverification=1 origin=strongkey.com auth requisite pam_succeed_if.so uid >= 1000 quiet_success auth required pam_deny.so # End of StrongKey MFA modificationsNOTE: Even though the lines highlighted in red are shown on three separate lines, this is only due to the width of the page. The lines in red must be on the same line in the file.
-
Configure FIDO login for console login (Run level 3) access by making the following modifications to /etc/pam.d/login file.
Replace the following line: auth substack system-auth with the following block of code (Replace strongkey.com origin with the relevant value) #auth substack system-auth auth required pam_env.so auth required pam_faildelay.so delay=2000000 auth [success=1 default=ignore] pam_succeed_if.so user ingroup mfausers auth sufficient pam_unix.so nullok try_first_pass auth [success=2 default=ignore] pam_succeed_if.so user notingroup mfausers auth requisite pam_unix.so nullok try_first_pass auth sufficient pam_u2f.so authfile=/etc/strongkey/fido-keys debug debug_file=/var/log/pamfido.log cue pinverification=1 origin=strongkey.com auth requisite pam_succeed_if.so uid >= 1000 quiet_success auth required pam_deny.so # End of StrongKey MFA modificationsNOTE: Even though the lines highlighted in red are shown on three separate lines, this is only due to the width of the page. The lines in red must be on the same line in the file.
-
Configure FIDO login for Graphical console login (Run level 5) access by making the following modifications to /etc/pam.d/gdm-password file.
 NOTE: This section is only necessary if the machine has a full installation of Rocky/RHEL with GUI, and should be skipped on minimal installations.
NOTE: This section is only necessary if the machine has a full installation of Rocky/RHEL with GUI, and should be skipped on minimal installations.Replace the following line:
auth include password-auth with the following block of code (Replace strongkey.com origin with the relevant value) #auth include password-auth auth required pam_env.so auth required pam_faildelay.so delay=2000000 auth [success=1 default=ignore] pam_succeed_if.so user ingroup mfausers auth sufficient pam_unix.so nullok try_first_pass auth [success=2 default=ignore] pam_succeed_if.so user notingroup mfausers auth requisite pam_unix.so nullok try_first_pass auth sufficient pam_u2f.so authfile=/etc/strongkey/fido-keys debug debug_file=/var/log/pamfido.log cue pinverification=1 origin=strongkey.com auth requisite pam_succeed_if.so uid >= 1000 quiet_success auth required pam_deny.so # End of StrongKey MFA modificationsNOTE: Even though the lines highlighted in red are shown on three separate lines, this is only due to the width of the page. The lines in red must be on the same line in the file.
-
Restore context to the fido-keys file in /etc/strongkey/ to make sure it has permission to be used during login. This command must be run as root.
restorecon /etc/strongkey/fido-keys
